Did you know that Symantec surveyed small and medium-sized businesses (SMBs) and found that 21% considered cyber security a “nice to have” feature? Does that concern you a little bit?
The cost of cybercrime in the United States is staggering. Check out these numbers! According to Ponemon Institute; Hewlett-Packard (HP Enterprise Security), these are the costs last year (2015) for each industry, in million US dollars:
-
Financial services: 28.33
-
Energy and utilities: 27.62
-
Defense and aerospace: 23.18
-
Technology: 16.45
-
Communications: 14.9
-
Services: 12.93
-
Transportation: 12.08
-
Retail: 11.96
-
Education and research: 11.41
-
Industrial: 11.02
-
Healthcare: 9.78
-
Public sector: 9.37
-
Consumer products: 8.68
-
Hospitality: 8.23
That’s over 200 million dollars combined!
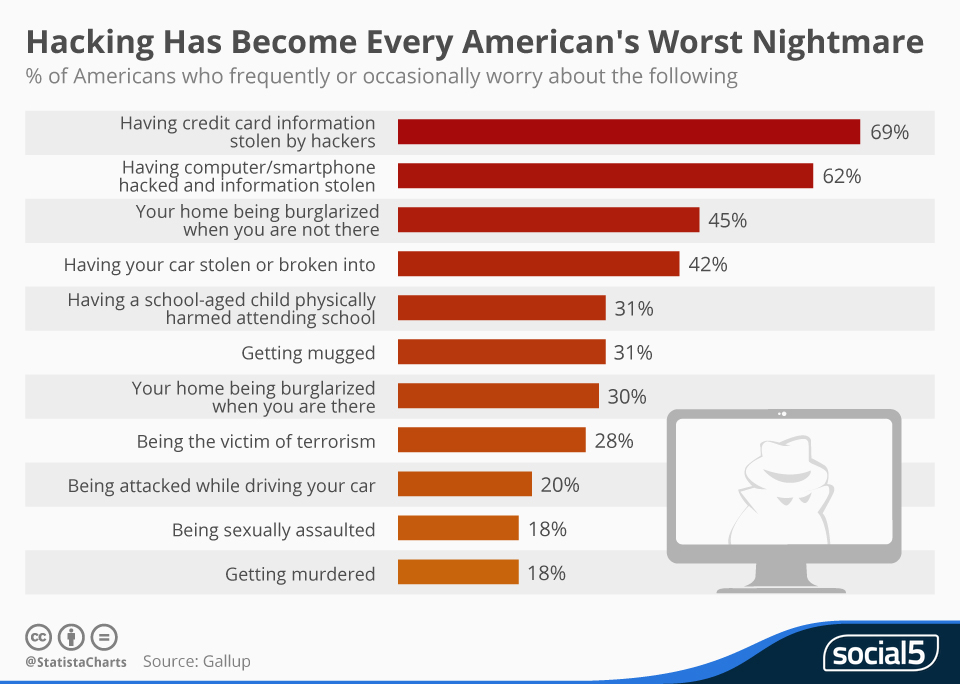
In contrast to the somewhat relaxed attitude of SMBs over cybersecurity, individual Americans have a completely different attitude about it. Cybercrime takes the top two spots for the crimes consumers worry the most about!
Ponemon Institute and HP found that 100% of businesses have suffered attacks caused by viruses, worms or trojans. Every single business has dealt with this! Perhaps cybersecurity isn’t really a “nice to have” feature. Of the businesses surveyed, 97% had also experienced malware attacks.
This means that your business will deal with the fall out of cybercrime, guaranteed! The forecast states 100% chance of storms. Start with the following steps to prepare:
-
Backup your data! Don’t learn this the hard way after an expensive loss. Set up regular backups in a secure location away from your hosted data (such as the cloud).
-
Set up multifactor authentication and require it of every employee.
-
Train everyone on security. It should be part of every single employee’s job description today: understand and know what they should do to protect themselves and the company from cyber threats. Teach them about phishing, malware, viruses, etc.
-
Be aware of what you send via email. Treat it as though anything you attach or write could be posted on a public forum.
-
Have a definite plan for responding to breaches.
-
Use the free resources provided by the US Small Business Association for cybersecurity.
-
Know when to get an expert to help. If you don’t have the knowledge from your staff to test website security, conducting risk assessments or defining a cybersecurity breach procedure, hire an IT Consultant.
We have an enterprise security solution to protect your network and vital data through ongoing monitoring and support. Don’t waste another minute thinking this is simply “nice to have.” You are statistically at risk, so take the steps to limit your risk and exposure today.

 Have you heard of shadow IT? Sounds like the no-good-broad-shouldered-thug that you don’t want to meet in a dark alley. You may be creating shadow IT at your company if your software is outdated, your policies are complicated or you’re lacking in IT support. Do you ever hear whispered conversations about how it’s not worth it to call the help desk because they won’t get around to helping for days? You may be breeding dark alleys and shadow IT.
Have you heard of shadow IT? Sounds like the no-good-broad-shouldered-thug that you don’t want to meet in a dark alley. You may be creating shadow IT at your company if your software is outdated, your policies are complicated or you’re lacking in IT support. Do you ever hear whispered conversations about how it’s not worth it to call the help desk because they won’t get around to helping for days? You may be breeding dark alleys and shadow IT.